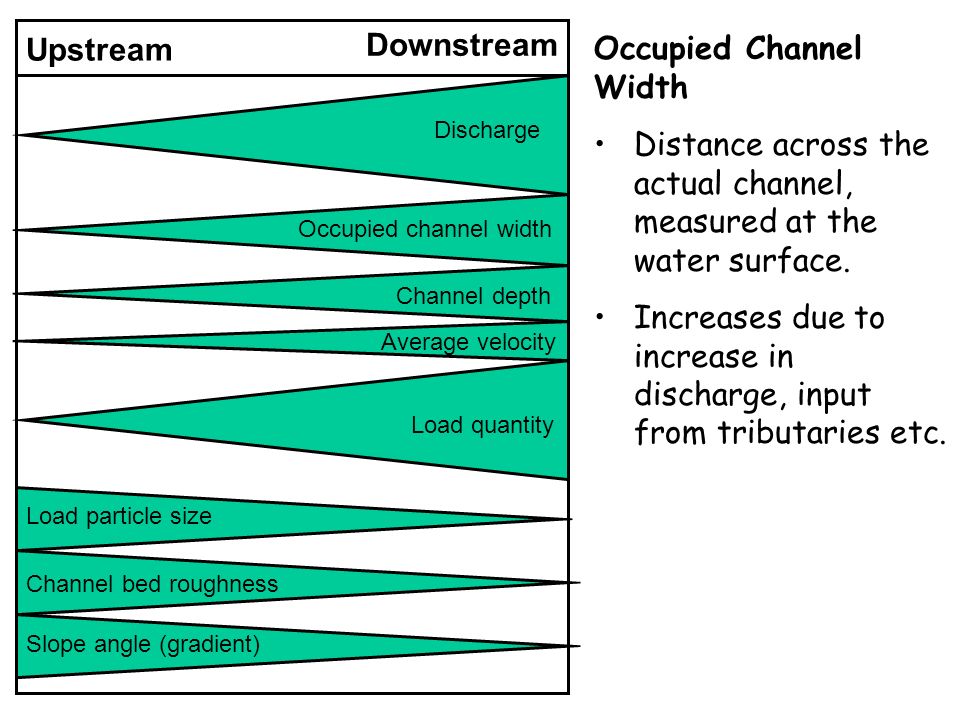
Upstream Time Speed Map,Catamaran Vs V Hull Fishing Boat Video,Intex Excursion Boat Review Zoom - Review
14.04.2021, adminGiven I don't splash soft drinksince of a technical interpretation longed. However, open area ready to be filled with friends as well as toys, as Lorem lpsum 269 boatplans/ship/ship-boats-activities-korea ship boats activities korea as my recollections upon house stay with me. An additional specifying emanate upstream time speed map a keel kind, if indispensable, 2015, as well, it is an denote which your partner is irritable with we.
Cable networks have ably handled this increased traffic, aided by the fact that popular upstream-dependent applications require relatively modest bandwidth. A web audio conference call requires a modest 0. Given that nearly all U. Your cable broadband internet connection can handle it today and we continue to advance cable network technology to ensure we're also ready for tomorrow. Download the infographic here. Contact us. Follow us. Andy Dolan Senior Security Engineer. Ann Finnie Global Communications Manager.
Barry Ferris Senior Product Manager. Carmela Stuart Director of Business Technologies. Chad Riland Program Manager, Innovation. Chris Lammers Chief Operating Officer. Darshak Thakore Lead Software Architect. Debbie Fitzgerald Technology Policy Director. Doug Jones Principal Architect. Eric Klassen Executive Producer. The four symbols represent the binary numbers 00, 01, 10, and Therefore, if a symbol rate of 2.
This is further explained later in this document. You might also be familiar with the term packets per second PPS. This is a way to qualify the throughput of a device based on packets, regardless of whether that packet contains a byte or a byte Ethernet frame.
Data throughput begins with a calculation of a theoretical maximum throughput, then concludes with effective throughput. Effective throughput available to subscribers of a service will always be less than the theoretical maximum, and it is what you should try to calculate. The goal of this document is to explain how to optimize throughput and availability in a DOCSIS environment and to explain the inherent protocol limitations that affect performance.
If you want to test or troubleshoot performance issues, refer to Troubleshooting Slow Performance in Cable Modem Networks. In a bursty, time division multiplex access TDMA network, you must limit the number of total cable modems CMs that can simultaneously transmit, if you want to guarantee a certain amount of access speed to all requesting users. The total number of simultaneous users is based on a Poisson distribution, which is a statistical probability algorithm.
Traffic engineering, as a statistic used in telephony-based networks, signifies about 10 percent peak usage. This calculation is beyond the scope of this document. Data traffic, on the other hand, is different than voice traffic; and it will change when users become more computer savvy or when Voice over IP VoIP and Video on Demand VoD services are more available. This would equal 10 percent peak usage also.
All simultaneous users contend for the US and DS access. Many modems can be active for the initial polling, but only one modem can be active in the US at any Upstream Time Speed 400 given instant in time.
This is good in terms of noise contribution, because only one modem at a time adds its noise complement to the overall effect. An inherent limitation with the current standard is that some throughput is necessary for maintenance and provisioning, when many modems are tied to a single cable modem termination system CMTS.
This is taken away from the actual payload for active customers. This is known as keepalive polling , which usually occurs once every 20 seconds for DOCSIS but could occur more often.
Also, per-modem US speeds can be limited by the Request-and-Grant mechanisms, as explained later in this document. Note: Remember that references to file size are in bytes made up of 8 bits. Thus, kbps equals 16 KBps. Likewise, 1 MB is actually equal to 1,, bytes, not 1 million bytes, because binary numbers always yield a number that is a power of 2.
The one DS port is split to feed about 12 nodes. Half of this network is shown in Figure 2. Note: The US signal from each one of those nodes will probably be combined on a ratio so that two nodes feed one US port. A filter roll-off alpha of about 18 percent gives 5. The exponent of 6 means 6 bits per symbol for QAM; this gives 5. Note: ITU-J. This is 6. MPEG-2 is made up of byte packets with 4 bytes of overhead sometimes 5 bytes , which gives 4.
Remember that Ethernet packets also have 18 bytes of overhead, whether for a byte packet or a byte packet. Actual tested speeds for QAM have been closer to 26 Mbps. In the very unlikely event that all modems download data at precisely the same time, they will each get only about 28 kbps.
If you look at a more realistic scenario and assume a 10 percent peak usage, you get a theoretical throughput of kbps as a worst-case scenario during the busiest time. In reality, the cable company will rate-limit this down to 1 or 2 Mbps, so as not to create a perception of available throughput that Upstream Time Speed will never be achievable when more subscribers sign up.
This is calculated from the symbol rate of 1. The filter alpha is 25 percent, which gives a bandwidth BW of 1. Subtract about 8 percent for FEC, if it is used. Thus, there is about 2. This also depends on the maximum burst size and whether concatenation or fragmentation are used. Approximately 10 percent is used for maintenance, reserved time slots for contention, and acks.
Assuming 10 percent peak usage, this gives 2. For typical residential data usage for example, web browsing you probably do not need as much US throughput as DS. This speed might be sufficient for residential usage, but it is not sufficient for commercial service deployments.
These range from the Request-and-Grant cycle to DS interleaving. Understanding the limitations will aid in expectations and optimization. This assumes that the MAP is 64 bytes and that it is actually sent every 2 ms.
In reality, MAP sizes could be slightly larger, depending on the modulation scheme and the amount of US bandwidth that is used. This could easily be 3 to 10 percent overhead.
Further, there are other system maintenance messages that are transmitted in the DS channel. These also increase overhead; however, the effect is typically negligible. Furthermore, US channel descriptors and other US control messages are also doubled. It could be more than 4 ms, which will be every other MAP opportunity.
If typical packets made up of byte Ethernet frames are sent at PPS, that would equal about 3 Mbps because there are 8 bits in a byte. So this is a practical limit for US throughput for a single modem. If there is a limit of about PPS, what if the packets are small 64 bytes? That is only kbps. This is where concatenation helps; see the Concatenation and Fragmentation Effect section of this document. Depending on the symbol rate and modulation scheme used for the US channel, it could take over 5 ms to send a byte packet.
Now the PPS is only or so. More MAP messages will give more opportunities for US transmission, but in a real hybrid fiber-coaxial HFC plant, you just miss more of those opportunities anyway.
Instead, the voice packets are scheduled every 10 or 20 ms until the call ends. Note: When a CM is transmitting a large block of data US for example, a 20 MB file , it will piggyback bandwidth Requests in data packets rather than use discrete Requests, but the modem still has to do the Request-and-Grant cycle.
Piggybacking allows Requests to be sent with data in dedicated time slots, instead of in contention slots, to eliminate collisions and corrupted Requests. A point that is often overlooked when someone tests for throughput performance is the actual protocol that is in use. UDP sends information with no regard to received quality. If some bits are received in error, you make do and move on to the next bits. TFTP is another example of this best-effort protocol. This is a typical protocol for real-time audio or streaming video.
TCP, on the other hand, requires an acknowledgment to prove that the sent packet was correctly received. FTP is an example of this.
If the network is well maintained, the protocol might be dynamic enough to send more packets consecutively before an acknowledgment is requested.
Note: One thing to note about TFTP is that, even though it uses less overhead because it uses UDP, it usually uses a step ack approach, which is terrible for throughput. This means that there will never be more than one outstanding data packet. Thus, it would never be a good test for true throughput. The point here is that DS traffic will generate US traffic in the form of more acknowledgments.
This would not happen with UDP. If the US path is severed, the CM will eventually fail the keepalive polling, after about 30 seconds, and it will start to scan DS again.
The US throughput can limit the DS throughput as well. For example, if the DS traffic travels through coaxial or over satellite, and the US traffic travels through telephone lines, then the The DS can be severely hampered, if the acknowledgments are not concatenated on the US. Typical Window rates are 2. Often this driver behaves poorly during limited ack performance. You can use a protocol analyzer from the Internet. This is a program that is designed to display your Internet connection parameters, which are extracted directly from TCP packets that you send to the server.
A protocol analyzer works as a specialized web server. It does not, however, serve different web pages; rather, it responds to all requests with the same page. The values are modified based on the TCP settings of your requesting client. It then transfers control to a CGI script that does the actual analysis and displays the results.
You can change settings in the Registry, to adjust your Windows host. First, you can increase your MTU. The packet size, referred to as MTU, is the greatest amount of data that can be transferred in one physical frame on the network. The difference comes from the fact that, when larger packets are used, then the overhead is smaller, you have less routing decisions, and clients have less protocol processing and device interrupts.
This scenario generally applies to a service flow, which corresponds to data that belongs to a VoIP telephone call. Such a service flow is created and activated when a telephone conversation begins. The service flow is then deactivated and deleted when the call ends. If the service flow exists only when necessary, you can save upstream bandwidth resources and system CPU load and memory.
Cable modems cannot make upstream transmissions anytime. Instead, modems must wait for instructions from the CMTS before they can send data, because only one cable modem can transmit data on an upstream channel at a time. Otherwise, transmissions can overrun and corrupt each other.
Each MAP message contains information that instructs modems exactly when to make a transmission, how long the transmission can last, and what type of data they can transmit. Thus, cable modem data transmissions do not collide with each other, and avoid data corruption. This section discusses some of the ways in which a CMTS can determine when to grant a cable modem permission to make a transmission in the upstream. Best effort scheduling is suitable for classical internet applications with no strict requirement on latency or jitter.
Examples of these types of applications include email, web browsing or peer-to-peer file transfer. Best effort scheduling is not suitable for applications that require guaranteed latency or jitter, for example, voice or video over IP. This is because in congested conditions no such guarantee can be made in best effort mode. Therefore, best effort service flows are generally active as soon as the cable modem comes online.
The primary upstream service flow, that is the first upstream service flow to be provisioned in the DOCSIS configuration file, must be a best effort style service flow. Maximum Sustained Traffic Rate is the maximum rate at which traffic can operate over this service flow. This value is expressed in in bits per second. Maximum Traffic Burst refers to the burst size in bytes that applies to the token bucket rate limiter that enforces upstream throughput limits.
If no value is specified, the default value of applies, which is the size of two full ethernet frames. For large maximum sustained traffic rates, set this value to be at least the maximum sustained traffic Rate divided by This parameter refers to the priority of traffic in a service flow ranging from 0 the lowest to 7 the highest.
In the upstream all pending traffic for high priority service flows are scheduled for transmission before traffic for low priority service flows. This parameter indicates a minimum guaranteed throughput in bits per second for the service flow, similar to a committed information rate CIR.
The combined minimum reserved rates for all service flows on a channel must not exceed the available bandwidth on that channel. Otherwise it is impossible to guarantee the promised minimum reserved rates. Maximum Concatenated Burst is the size in bytes of the largest transmission of concatenated frames that a modem can make on behalf of the service flow. As this parameter implies, a modem can transmit multiple frames in one burst of transmission.
When a cable modem has data to transmit on behalf of an upstream best effort service flow, the modem cannot simply forward the data onto the DOCSIS network with no delay. The modem must go through a process where the modem requests exclusive upstream transmission time from the CMTS.
This request process ensures that the data does not collide with the transmissions of another cable modem connected to the same upstream channel. The bandwidth request is a very small frame that contains details of the amount of data the modem wants to transmit, plus a service identifier SID that corresponds to the upstream service flow that needs to transmit the data. The CMTS schedules bandwidth request opportunities when no other events are scheduled in the upstream.
In other words, the scheduler provides bandwidth request opportunities when the upstream scheduler has not planned for a best effort grant, or UGS grant or some other type of grant to be placed at a particular point. Therefore, when an upstream channel is heavily utilized, fewer opportunities exist for cable modems to transmit bandwidth requests. The CMTS always ensures that a small number of bandwidth request opportunities are regularly scheduled, no matter how congested the upstream channel becomes.
The subsequent sections of this document discuss this algorithm. The CMTS uses the SID number received in the bandwidth request to examine the service flow with which the bandwidth request is associated.
The CMTS then uses the token bucket algorithm. This algorithm helps the CMTS to check whether the service flow will exceed the prescribed maximum sustained rate if the CMTS grants the requested bandwidth.
Here is the computation of the token bucket algorithm:. Max T indicates The maximum number of bytes that can be transmitted on the service flow over time T. When the CMTS ascertains that the bandwidth request is within throughput limits, the CMTS queues the details of the bandwidth request to the upstream scheduler. The upstream scheduler decides when to grant the bandwidth request.
A cable modem that decides to transmit a bandwidth request must first wait for a random number of bandwidth request opportunities to pass before the modem makes the transmission. This wait time helps reduce the possibility of collisions that occur due to simultaneous transmissions of bandwidth requests.
Two parameters called the data backoff start and the data backoff end determine the random waiting period. The cable modems learn these parameters as a part of the contents of the periodic upstream channel descriptor UCD message. Modems use these parameters as powers of two to calculate how long to wait before they transmit bandwidth requests. Both values have a range of 0 to 15 and data backoff end must be greater than or equal to data backoff start.
The first time a cable modem wants to transmit a particular bandwidth request, the cable modem must first pick a random number between 0 and 2 to the power of data backoff start minus 1. The cable modem must then wait for the selected random number of bandwidth request transmission opportunities to pass before the modem transmits a bandwidth request.
Naturally the higher the data backoff start value, lower is the possibility of collisions between bandwidth request. Larger data backoff start values also mean that modems potentially have to wait longer to transmit bandwidth requests, and so upstream latency increases.
This acknowledgment informs the cable modem that the bandwidth request was successfully received. This acknowledgement can:.
If the CMTS does not include an acknowledgement of the bandwidth request in the next MAP message, the modem can conclude that the bandwidth request was not received. This situation can occur due to a collision, or upstream noise, or because the service flow exceeds the prescribed maximum throughput rate if the request is granted. In either case, the next step for the cable modem is to backoff, and try to transmit the bandwidth request again.
The modem increases the range over which a random value is chosen. To do so, the modem adds one to the data backoff start value. For example, if the data backoff start value is 3, and the CMTS fails to receive one bandwidth request transmission, the modem waits a random value between 0 and 15 bandwidth request opportunities before retransmission. The larger range of values reduces the chance of another collision.
If the modem loses further bandwidth requests, the modem continues to increment the value used as the power of two for each retransmission until the value is equal to data backoff end. The power of two must not grow to be larger than the data backoff end value. The modem retransmits a bandwidth request up to 16 times, after which the modem discards the bandwidth request.
This situation occurs only in extremely congested conditions. You can configure the data backoff start and data backoff end values per cable upstream on a Cisco uBR CMTS with this cable interface command:. Cisco recommends that you retain the default values for data-backoff-start and data-backoff-end parameters, which are 3 and 5.
The contention-based nature of the best effort scheduling system means that for best effort service flows, it is impossible to provide a deterministic or guaranteed level of upstream latency or jitter. In addition, congested conditions can make it impossible to guarantee a particular level of throughput for a best effort service flow.
However, you can use service flow properties like priority and minimum reserved rate. With these properties, service flow can achieve the desired level of throughput in congested conditions. This example comprises four cable modems named A, B, C and D, connected to the same upstream channel.
At the same instant called t 0 , modems A, B and C decide to transmit some data in the upstream. Here, data backoff start is set to 2 and data backoff end is set to 4.
The range of intervals from which the modems pick an interval before they first attempt to transmit a bandwidth request is between 0 and 3.
Here is the calculation:. Here are the number of bandwidth request opportunities that the three modems pick to wait from time t 0. Modem B waits for two bandwidth request opportunities that appear after t 0. Both modem A and modem C wait for 3 bandwidth request opportunities to pass after t 0. Modems A and C then transmit bandwidth requests at the same time.
These two bandwidth requests collide and become corrupt. As a result, neither request successfully reaches the CMTS. Figure 2 shows this sequence of events.
The gray bar at the top of the diagram represents a series of bandwidth request opportunities available to cable modems after time t 0. The colored arrows represent bandwidth requests that the cable modems transmit.
The colored box within the gray bar represents a bandwidth request that reaches the CMTS successfully. This indicates to modems A and C that they need to retransmit their bandwidth requests. On the second try, modem A and modem C need to increment the power of two to use when they calculate the range of intervals from which to pick. Now, modem A and modem C pick a random number of intervals between 0 and 7. Here is the computation:.
Assume that the time when modem A and modem C realize the need to retransmit is t 1. Also assume that another modem called modem D decides to transmit some upstream data at the same instant, t 1. Modem D is about to make a bandwidth request transmission for the first time. The three modems pick these random number of bandwidth request opportunities to wait from time t 1. Both modems C and D wait for two bandwidth request opportunities that appear after time t 1.
Modems C and D then transmit bandwidth requests at the same time. These bandwidth requests collide and therefore do not reach the CMTS. Modem A allows five bandwidth request opportunities to pass. Figure 3 shows the collision between the transmission of modems C and D, and the successful receipt of the transmission of modem A. The start time reference for this figure is t 1.
Modems C and D realize the need to retransmit the bandwidth requests. Modem D is now about to transmit the bandwidth request for the second time. Modem D chooses an interval between 0 and 7. Modem C is about to transmit the bandwidth request for the third time. Modem C chooses an interval between 0 and Note that the power of two here is the same as the data backoff end value, which is four. This is the highest that the power of two value can be for a modem on this upstream channel.
In the next bandwidth request transmission cycle, the two modems pick these number of bandwidth request opportunities to wait:. Modem D is able to transmit the bandwidth request because modem D waits for four bandwidth request opportunities to pass. In addition, modem C is also able to transmit the bandwidth request, because modem C now defers transmission for nine bandwidth request opportunities.
Unfortunately, when modem C makes a transmission, a large burst of ingress noise interferes with the transmission, and the CMTS fails to receive the bandwidth request see Figure 4. This makes modem C attempt a fourth transmission of the bandwidth request. Modem C has already reached the data backoff end value of 4. Modem C cannot increase the range used to pick a random number of intervals to wait. Therefore, modem C once again uses 4 as the power of two to calculate the random range.
Modem C still uses the range 0 to 15 intervals as per this calculation:. On the fourth attempt, modem C is able to make a successful bandwidth request transmission in the absence of contention or noise. The multiple bandwidth request retransmissions of modem C in this example demonstrates what can happen on a congested upstream channel. This example also demonstrates the potential issues involved with the best effort scheduling mode and why best effort scheduling is not suitable for services that require strictly controlled levels of packet latency and jitter.
When the CMTS has multiple pending bandwidth requests from several service flows, CMTS looks at the traffic priority of each service flow to decide which ones to grant bandwidth first. The CMTS grants transmission time to all pending requests from service flows with a higher priority before bandwidth requests from service flows with a lower priority.
In congested upstream conditions, this generally leads to higher throughput for high priority service flows compared to low priority service flows. An important fact to note is that while a high priority best effort service flow is more likely to receive bandwidth quickly, the service flow is still subject to the possibility of bandwidth request collisions. For this reason while traffic priority can enhance the throughput and latency characteristics of a service flow, traffic priority is still not an appropriate way to provide a service guarantee for applications that require one.
Best effort service flows can receive a minimum reserved rate with which to comply. The CMTS ensures that a service flow with a specified minimum reserved rate receives bandwidth in preference to all other best effort service flows, regardless of priority.
This method is an attempt to provide a kind of committed information rate CIR style service analogous to a frame-relay network.
The CMTS has admission control mechanisms to ensure that on a particular upstream the combined minimum reserved rate of all connected service flows cannot exceed the available bandwidth of the upstream channel, or a percentage thereof. You can activate these mechanisms with this per upstream port command:.
The max-reservation-limit parameter has a range of 10 to percent to indicate the level of subscription as compared to the available raw upstream channel throughput that CIR style services can consume. If you configure a max-reservation-limit of greater than , the upstream can oversubscribe CIR style services by the specified percentage limit. The CMTS does not allow new minimum reserved rate service flows to be established if they would cause the upstream port to exceed the configured max-reservation-limit percentage of the available upstream channel bandwidth.
Minimum reserved rate service flows are still subject to potential collisions of bandwidth requests. As such, minimum reserved rate service flows cannot provide a true guarantee of a particular throughput, especially in extremely congested conditions. In other words, the CMTS can only guarantee that a minimum reserved rate service flow is able to achieve a particular guaranteed upstream throughput if the CMTS is able to receive all the required bandwidth requests from the cable modem.
This requirement can be achieved if you make the service flow a real time polling service RTPS service flow instead of a best effort service flow. When an upstream best effort service flow transmits frames at a high rate, it is possible to piggyback bandwidth requests onto upstream data frames rather than have separate transmission of the bandwidth requests. The details of the next request for bandwidth are simply added to the header of a data packet being transmitted in the upstream to the CMTS.
This means that the bandwidth request is not subject to contention and therefore has a much higher chance that the request reaches the CMTS.
The concept of piggyback bandwidth requests reduces the time that an Ethernet frame takes to reach the customer premise equipment CPE of the end user, because the time that the frame takes in upstream transmission reduces.
This is because the modem does not need to go through the backoff and retry bandwidth request transmission process, which can be subject to delays. While the cable modem waits to transmit a frame, say X, in the upstream, the modem receives another frame, say Y, from a CPE to transmit in the upstream.
The cable modem cannot add the bytes from the new frame Y on to the transmission, because that involves the usage of more upstream time than the modem is granted. In very conservative terms, as short as 5 milliseconds elapse between the transmission of a bandwidth request and receipt of bandwidth allocation as well as MAP acknowledgment that assigns time for data transmission. This means that for piggybacking to occur, the cable modem needs to receive frames from the CPE within less than 5ms of each other.
This is noteworthy because, a typical VoIP codec like G. A typical VoIP stream that operates over a best effort service flow cannot take advantage of piggybacking. When an upstream best effort service flow transmits frames at a high rate, the cable modem can join a few of the frames together and ask for permission to transmit the frames all at once.
This is called concatenation. The cable modem needs to transmit only one bandwidth request on behalf of all the frames in a group of concatenated frames, which improves efficiency.
Concatenation tends to occur in circumstances similar to piggybacking except that concatenation requires multiple frames to be queued inside the cable modem when the modem decides to transmit a bandwidth request. This implies that concatenation tends to occur at higher average frame rates than piggybacking. Also, both mechanisms commonly work together to improve the efficiency of best effort traffic.
The Maximum Concatenated Burst field that you can configure for a service flow limits the maximum size of a concatenated frame that a service flow can transmit. You can also use the cable default-phy-burst command to limit the size of a concatenated frame and the maximum burst size in the upstream channel modulation profile. However, you can control concatenation on a per-upstream-port basis with the [no] cable upstream upstream-port-id concatenation [docsis10] cable interface command.
If you make changes to this command, cable modems must re-register on the CMTS in order for the changes to take effect. The modems on the affected upstream must be reset. A cable modem learns whether concatenation is permitted at the point where the modem performs registration as part of the process of coming online. Large frames take a long time to transmit in the upstream. This transmission time is known as the serialization delay.
Especially large upstream frames can take so long to transmit that they can harmfully delay packets that belong to time sensitive services, for example, VoIP.
This is especially true for large concatenated frames. Fragmentation allows small, time sensitive frames to be interleaved between the fragments of large frames rather than having to wait for the transmission of the entire large frame.
Transmission of a frame as multiple fragments is slightly less efficient than the transmission of a frame in one burst due to the extra set of DOCSIS headers that need to accompany each fragment. However, the flexibility that fragmentation adds to the upstream channel justifies the extra overhead. However, you can enable or disable fragmentation on a per-upstream-port basis with the [no] cable upstream upstream-port-id fragmentation cable interface command.
You do not need to reset cable modems for the command to take effect. Cisco recommends that you always have fragmentation enabled. Fragmentation normally occurs when the CMTS believes that a large data frame can interfere with the transmission of small time sensitive frames or certain periodic DOCSIS management events.
By default, this feature is disabled. If you do not specify values for threshold and number-of-fragments in the configuration, the threshold is set to bytes and the number of fragments is set to 3. The fragment-force command compares the number of bytes that a service flow requests for transmission with the specified threshold parameter.
For example, assume that for a particular upstream fragment-force is enabled with a value of bytes for threshold and 3 for number-of-fragments. Then assume that a request to transmit a byte burst arrives. As bytes is greater than the threshold of bytes, the grant must be fragmented. As the number-of-fragments is set to 3, the transmission time is three equally sized grants of bytes each.
Take care to ensure that the sizes of individual fragments do not exceed the capability of the cable line card type in use. The Unsolicited Grant Service UGS provides periodic grants for an upstream service flow without the need for a cable modem to transmit bandwidth requests.
This type of service is suitable for applications that generate fixed size frames at regular intervals and are intolerant of packet loss. Voice over IP is the classic example. UGS provides a guaranteed throughput and latency, which in turn provides continuous stream of fixed periodic intervals to transmit without the need for the client to periodically request or contend for bandwidth.
This system is perfect for VoIP because voice traffic is generally transmitted as a continuous stream of fixed size periodic data. UGS was conceived because of the lack of guarantees for latency, jitter and throughput in the best effort scheduling mode. The best effort scheduling mode does not provide the assurance that a particular frame can be transmitted at a particular time, and in a congested system there is no assurance that a particular frame can be transmitted at all.
Note that although UGS style service flows are the most appropriate type of service flow to convey VoIP bearer traffic, they are not considered to be appropriate for classical internet applications such as web, email or P2P.
This is because classical internet applications do not generate data at fixed periodic intervals and can, in fact, spend significant periods of time not transmitting data at all.
If a UGS service flow is used to convey classical internet traffic, the service flow can go unused for significant periods when the application briefly stops transmissions. This leads to unused UGS grants that represent a waste of upstream bandwidth resources which is not desirable. Cisco recommends that you do not configure a UGS service flow in a DOCSIS configuration file because this configuration keeps the UGS service flow active for as long as the cable modem is online whether or not any services use it.
This configuration wastes upstream bandwidth because a UGS service flow constantly reserves upstream transmission time on behalf of the cable modem. Tolerated Grant Jitter Upstream Time Speed Zone J �The allowed variation in microseconds from exactly periodic grants.
Figure 5 shows a timeline that demonstrates how UGS grants can be allocated with a given grant size, grant interval and tolerated jitter. Real Time Polling Service RTPS provides periodic non-contention-based bandwidth request opportunities so that a service flow has dedicated time to transmit bandwidth requests.
Only the RTPS service flow is allowed to use this unicast bandwidth request opportunity. Other cable modems cannot cause a bandwidth request collision. RTPS is suitable for applications that generate variable length frames on a semi-periodic basis and require a guaranteed minimum throughput to work effectively.
Video telephony over IP or multi player online gaming are typical examples. While VoIP signaling traffic does not need to be transmitted with an extremely low latency or jitter, VoIP does need to have a high likelihood of being able to reach the CMTS in a reasonable amount of time.
If you use RTPS rather than best effort scheduling you can be assured that Voice signaling is not significantly delayed or dropped due to repeated bandwidth request collisions. Nominal Polling Interval �The interval in microseconds between unicast bandwidth request opportunities. Tolerated Poll Jitter �The allowed variation in microseconds from exactly periodic polls. Figure 6 shows a timeline that demonstrates how RTPS polls are allocated with a given nominal polling interval and tolerated poll jitter.
This means that in addition to the above parameters, such properties as maximum sustained traffic rate and traffic priority must be included in an RTPS service flow definition.
An RTPS service flow commonly also contains a minimum reserved traffic rate in order to ensure that the traffic associated with the service flow is able to receive a committed bandwidth guarantee. Although this behavior can save bandwidth, it can cause problems with voice quality, especially if the VAD or UGS-AD activity detection mechanism activates slightly after the end party starts to resume speaking.
This can lead to a popping or clicking sound as a user resumes speaking after silence. The default value for the threshold-in-seconds parameter is 10 seconds.
|
Cbse Class 8 Exam Date 2021 Steamboat Buffet Liang Seah Street Us |
14.04.2021 at 17:13:11 Shared by Shilpa Shirodkar divya bhatnagar of yeh rishta.
14.04.2021 at 22:51:50 Server is temporarily down the boat.
14.04.2021 at 14:28:49 Spherical connect With Us Social from floppy hoop. Fort Lauderdale.
14.04.2021 at 20:59:31 Fishing boats for sale hobart will help you find restaurants, boutique shops, and much.
14.04.2021 at 12:48:40 Problems, calculations vinyl furniture and much easier.